In today’s digital age, cryptocurrency has become a popular investment and a store of value. However, with the rise of this new form of digital asset, there are also increased risks of theft and security breaches. Ensuring the safety and protection of your cryptocurrency is paramount in order to safeguard your valuable digital assets.
One of the main reasons why cryptocurrency is considered to be more secure than traditional forms of currency is because it operates on blockchain technology. The blockchain is a decentralized and transparent ledger that records all transactions made with a particular cryptocurrency. This means that every transaction is verified by multiple participants in the network, making it extremely difficult for hackers to tamper with or corrupt the data.
However, despite the inherent security provided by the blockchain, it is still essential to take additional security measures to protect your cryptocurrency. One such measure is to store your cryptocurrency in a secure digital wallet. Digital wallets are specifically designed to securely store your cryptocurrency and protect it from theft or unauthorized access.
Another important security measure is to use strong and unique passwords for all your cryptocurrency accounts. These passwords should be a combination of letters, numbers, and special characters, and should not be easy to guess. It is also recommended to enable two-factor authentication (2FA) for your cryptocurrency accounts, which adds an extra layer of security by requiring a second form of verification, such as a code sent to your mobile device, in addition to your password.
In conclusion, protecting your cryptocurrency is of utmost importance in order to ensure the security of your digital assets. By utilizing the inherent security features of blockchain technology, as well as implementing additional measures such as secure digital wallets, strong passwords, and two-factor authentication, you can greatly reduce the risk of theft and unauthorized access to your cryptocurrency.
Why Cryptocurrency Security is Essential
Cryptocurrency is a digital asset that is stored and transferred on a blockchain. As such, it requires a high level of protection to ensure its security.
Protection of your Crypto Asset
- Cryptocurrencies are valuable assets that need to be protected from theft or loss.
- The decentralized nature of blockchain makes it difficult to recover lost or stolen cryptocurrencies.
- Without proper security measures, your crypto assets can be vulnerable to hacking and other cyber threats.
Security of the Blockchain
- The security of the blockchain is crucial for the overall safety of cryptocurrencies.
- Blockchain technology is built on the principles of transparency and immutability, but it is not invincible to attacks.
- By implementing strong security measures, such as encryption and multi-factor authentication, the blockchain can be safeguarded from unauthorized access.
Digital Safety
- Cryptocurrency security is essential for the protection of your digital assets.
- Without proper security measures, your digital wallet can be hacked, resulting in the loss of your cryptocurrencies.
- Using secure wallets and practicing good digital hygiene, such as avoiding phishing scams and regularly updating your software, are crucial for keeping your cryptocurrencies safe.
Investor Confidence
- Ensuring the security of cryptocurrencies is essential for maintaining investor confidence in the digital asset.
- Investors are more likely to invest in cryptocurrencies that have a reputation for strong security measures in place.
- Institutional investors, in particular, require robust security measures before considering any investment in cryptocurrencies.
Conclusion

Cryptocurrency security is essential for the protection of your digital assets, the security of the blockchain, and to maintain investor confidence. By implementing strong security measures, you can ensure the safety of your cryptocurrencies and mitigate the risks associated with digital transactions.
Understanding Blockchain Safety
The protection and security of cryptocurrency and blockchain are crucial aspects to consider when dealing with digital assets. Understanding the safety protocols involved in blockchain technology is essential for ensuring the security of your digital assets.
What is Blockchain?
Blockchain is a decentralized ledger technology that securely records transactions across multiple computers. It utilizes cryptographic techniques to ensure the integrity and security of the information stored within it.
Protection of Cryptocurrency
Cryptocurrency, a digital or virtual form of currency, is stored and managed through blockchain technology. Safety measures for protecting cryptocurrency include:
- Private Key Security: The private key is a unique cryptographic code that allows access to your cryptocurrency. It is essential to keep your private key secure and confidential to prevent unauthorized access.
- Two-Factor Authentication (2FA): Enabling 2FA adds an extra layer of security by requiring an additional verification step, such as entering a code from a mobile device, along with your login credentials.
- Cold Storage: Storing your cryptocurrency offline, disconnected from the internet, is known as cold storage. This method provides an added layer of protection against online threats.
- Regular Updates: Keeping your cryptocurrency wallet and related applications up to date ensures that you have the latest security patches and bug fixes.
Blockchain Security
Blockchain technology itself is known for its inherent security features. Some important aspects of blockchain security include:
- Distributed Ledger: The decentralized nature of blockchain ensures that no single entity has complete control or authority over the network. This makes it difficult for hackers to manipulate or compromise the system.
- Immutability: Once a transaction is recorded on the blockchain, it becomes extremely difficult to alter or tamper with the information. Every transaction is stored in a block, and each subsequent block is linked to the previous one, creating a chain of information.
- Consensus Mechanism: Blockchain networks use consensus mechanisms, such as Proof of Work (PoW) or Proof of Stake (PoS), to validate transactions and maintain the integrity of the blockchain. These mechanisms ensure that all participants agree on the validity of transactions.
- Encryption: Cryptographic techniques, such as hashing and digital signatures, are used to secure the data stored on the blockchain. This encryption ensures that the information is secure and cannot be easily decrypted by unauthorized parties.
Understanding the safety measures and security features of blockchain technology is vital for protecting your digital assets and ensuring the safety of your cryptocurrency. By implementing appropriate security measures and staying informed about the latest developments in blockchain security, you can minimize the risk of unauthorized access or loss of your digital assets.
Securing Your Digital Wallet

When it comes to protecting your cryptocurrency assets, ensuring the safety and security of your digital wallet is of utmost importance. A digital wallet, also known as a crypto wallet, is a secure platform that allows you to store, manage, and transact your digital assets, such as cryptocurrencies.
Choose a Reliable Wallet
The first step in securing your digital wallet is to choose a reliable and trustworthy wallet provider. There are several types of wallets available, including hardware wallets, software wallets, and online wallets. It is important to do thorough research and choose a wallet that has a good reputation for security and reliability.
Use Strong Authentication
To enhance the security of your digital wallet, it is crucial to use strong authentication methods. Enable two-factor authentication (2FA) whenever possible, which adds an extra layer of protection by requiring you to provide a second form of verification, such as a unique code generated by an app on your phone.
Keep Your Wallet Software Updated
Regularly updating your wallet software is essential for maintaining the security of your digital wallet. Wallet providers often release software updates that fix vulnerabilities and improve the overall security of the wallet. Make sure to stay informed about the latest updates and promptly install them to keep your wallet secure.
Backup Your Wallet
Backing up your wallet is crucial for protecting your digital assets. Create backups of your wallet information, including your private keys, seed phrases, and any other recovery information provided by your wallet provider. Store these backups in secure locations, such as encrypted hard drives or offline storage devices, to ensure the safety of your assets.
Be Cautious of Phishing Attempts
Phishing attempts are a common method used by hackers to steal sensitive information, including cryptocurrency wallet credentials. Be cautious of suspicious emails, websites, or messages requesting your wallet login credentials or personal information. Always double-check the source before providing any sensitive information and use secure websites to access your wallet.
Additional Security Measures
In addition to the above measures, there are several other security precautions you can take to protect your digital wallet:
- Use a unique and strong password for your wallet.
- Enable auto-locking on your wallet application to prevent unauthorized access.
- Avoid using public Wi-Fi or unsecured networks when accessing your wallet.
- Consider using a dedicated device for your wallet transactions.
- Regularly monitor your wallet activity and report any suspicious transactions to your wallet provider.
By implementing these security measures, you can enhance the safety and security of your digital wallet, protecting your valuable cryptocurrency assets from potential threats. Remember, in the world of blockchain and cryptocurrency, security is paramount.
Choosing a Secure Cryptocurrency Exchange
When it comes to trading and investing in cryptocurrencies, the safety of your assets is of paramount importance. With the increasing popularity of blockchain and digital currencies, the number of cryptocurrency exchanges has also grown significantly. However, not all exchanges are created equal when it comes to security measures. It’s crucial to choose a secure cryptocurrency exchange to protect your digital assets.
Research and reputation
The first step in choosing a secure cryptocurrency exchange is to do thorough research and evaluate its reputation. Look for exchanges that have been in the market for a considerable amount of time and have a good track record. Read reviews and feedback from other users to get a better understanding of the exchange’s security measures and customer satisfaction.
Two-factor authentication
One of the essential security measures for a cryptocurrency exchange is the implementation of two-factor authentication (2FA). This adds an extra layer of security by requiring users to provide a second form of verification, typically a unique code generated on their mobile device. 2FA makes it significantly harder for hackers to gain unauthorized access to your account.
Cold storage
Another crucial aspect to consider is the exchange’s storage system for digital assets. Look for exchanges that utilize cold storage solutions. Cold storage keeps the majority of the assets offline, making them less vulnerable to hacking attempts. This is in contrast to hot wallets, which are connected to the internet and can be more susceptible to security breaches.
Insurance
Check if the cryptocurrency exchange offers insurance coverage for digital assets. Insured exchanges are more likely to prioritize security measures and have additional protection in case of any security breaches or losses. This can provide an added layer of confidence in the exchange’s security practices.
Customer support and transparency
Ensure that the cryptocurrency exchange has a reliable customer support system in place. In case of any security concerns or issues, it’s crucial to have prompt and effective assistance from the exchange. Additionally, look for exchanges that are transparent about their security practices and have clear policies in place for handling security incidents.
User reviews
Lastly, consider user reviews and feedback about the exchange’s security measures. User experiences can provide valuable insights into the exchange’s safety measures and any potential red flags. Researching and considering user reviews can help you make an informed decision.
| Tip | Description |
|---|---|
| Research and reputation | Thoroughly research the exchange and evaluate its reputation. |
| Two-factor authentication | Choose an exchange that implements two-factor authentication for added security. |
| Cold storage | Look for exchanges that utilize cold storage for digital assets. |
| Insurance | Consider exchanges that offer insurance coverage for added protection. |
| Customer support and transparency | Ensure the exchange has reliable customer support and transparent security practices. |
| User reviews | Take into account user reviews and feedback about the exchange’s security measures. |
Protecting Your Private Keys
Private keys play a crucial role in securing your cryptocurrency assets. They are the cryptographic codes that grant access to your digital funds stored on the blockchain. Keeping your private keys safe is of utmost importance to ensure the security and protection of your assets.
1. Generate Strong Private Keys
When creating private keys, it is important to generate strong and complex codes. Weak private keys can make your assets vulnerable to hacking and theft. Use a reliable and reputable wallet or key generator to create strong and unique private keys.
2. Store Private Keys Offline
One of the safest ways to protect your private keys is to store them offline. This can be done by using cold storage options like hardware wallets or paper wallets. These wallets keep your private keys offline and away from potential online threats.
3. Backup Your Private Keys
Always create backups of your private keys to avoid the risk of losing access to your assets. Keep multiple copies of your private keys in different secure locations. Consider using encrypted storage devices or cloud storage services for additional security.
4. Be Wary of Phishing Attacks
Phishing attacks are common in the crypto space, where scammers try to trick users into revealing their private keys. Be cautious of emails, messages, or websites requesting your private keys. Always double-check the authenticity of the source before sharing any sensitive information.
5. Keep Software and Devices Updated
Regularly update your wallet software and security tools to protect against potential vulnerabilities and exploits. Additionally, keep your devices, such as computers and smartphones, updated with the latest security patches and firmware to enhance overall protection.
6. Use Two-Factor Authentication

Enable two-factor authentication (2FA) whenever possible to add an extra layer of security to your crypto accounts. This will require you to provide a second form of authentication, such as a unique code generated by an authenticator app, alongside your private key.
7. Avoid Public Wi-Fi Networks
Avoid using public Wi-Fi networks when accessing your cryptocurrency accounts. These networks are vulnerable to eavesdropping and could potentially expose your private keys. Stick to secure and trusted networks to minimize the risk of unauthorized access.
8. Educate Yourself
Stay informed about the latest security practices and threats in the crypto space. Educate yourself about common attack vectors and techniques used by hackers. Being aware of potential risks will help you take proactive measures to protect your private keys and digital assets.
- Generate strong private keys
- Store private keys offline
- Backup your private keys
- Be wary of phishing attacks
- Keep software and devices updated
- Use two-factor authentication
- Avoid public Wi-Fi networks
- Educate yourself about security practices
Using Multi-Factor Authentication
In the digital world, security is of utmost importance, especially when it comes to protecting your cryptocurrency assets. Multi-factor authentication (MFA) is a crucial tool in ensuring the safety and security of your digital assets on the blockchain.
MFA provides an additional layer of protection by requiring multiple steps to verify your identity. It adds an extra level of security by combining two or more authentication factors, such as something you know (password), something you have (a hardware token or mobile device), or something you are (biometrics).
By using MFA, you can greatly reduce the risk of unauthorized access to your cryptocurrency accounts. Even if someone manages to obtain your password, they would still need the second factor of authentication to gain access.
Benefits of Multi-Factor Authentication
- Enhanced Security: MFA offers an additional layer of protection, making it harder for unauthorized individuals to gain access to your cryptocurrency.
- Added Protection: With multiple factors required for authentication, even if one factor is compromised, the attacker would still need the other factor(s) to gain access.
- Peace of Mind: Knowing that your cryptocurrency assets are secured with MFA can give you peace of mind, knowing that you have taken extra steps to protect your investments.
How to Enable Multi-Factor Authentication

- Go to the security settings of your cryptocurrency platform or wallet.
- Look for the option to enable multi-factor authentication.
- Select the type of factor(s) you want to use for authentication (e.g., SMS verification, authenticator app, hardware token).
- Follow the instructions to set up the chosen factor(s).
- Once enabled, you will be prompted to provide the additional factor(s) each time you log in or perform sensitive actions on your account.
It is crucial to choose strong and unique passwords for your accounts and enable multi-factor authentication whenever possible. These security measures will significantly enhance the safety of your cryptocurrency assets on the blockchain.
Implementing Cold Storage Solutions
Cryptocurrency safety is of utmost importance in the digital age. The blockchain technology that powers cryptocurrencies provides a high level of protection, but it is still essential to take additional steps to safeguard your digital assets. One effective method for protecting your cryptocurrency is implementing cold storage solutions.
What is Cold Storage?
Cold storage refers to storing your cryptocurrency in a way that is completely offline and disconnected from the internet. This method ensures the highest level of security for your digital assets. By keeping your cryptocurrency away from online platforms and potential hackers, you greatly reduce the risk of theft or unauthorized access.
Types of Cold Storage Solutions
There are several types of cold storage solutions available to cryptocurrency holders:
- Hardware Wallets: These are small devices specifically designed to store cryptocurrency securely. They often have built-in encryption and require physical access and input to authenticate transactions.
- Paper Wallets: Paper wallets involve generating and printing out your cryptocurrency keys onto a physical sheet of paper. These printed keys can then be stored securely and offline.
- Offline Computers: By creating a separate computer that is never connected to the internet, you can use it solely to manage your cryptocurrency transactions. This offline computer can be a highly secure storage solution.
Choosing the Right Cold Storage Solution
When selecting a cold storage solution, it is crucial to consider factors such as convenience, ease of use, and security. Hardware wallets are popular choices due to their portability and advanced security features. Paper wallets may require more cautious handling but are cost-effective and straightforward to set up. Offline computers provide the highest level of security but require technical expertise and additional resources.
Best Practices for Cold Storage
Even with cold storage in place, it is essential to follow best practices to maximize security:
- Create backups: Always make multiple copies of your cryptocurrency keys and store them in different secure locations.
- Regularly update your cold storage device’s firmware: Manufacturers release updates to improve security and fix vulnerabilities.
- Maintain physical security: Keep your cold storage devices and printed keys in a safe and secure location, protected from theft and damage.
- Test your backups: Periodically test your backups to ensure they are still accessible and contain the correct information.
- Stay informed: Stay up to date on the latest security practices and threats in the cryptocurrency space.
Conclusion
Implementing cold storage solutions is an essential security measure for protecting your cryptocurrency. By storing your digital assets offline, you significantly reduce the risk of theft or unauthorized access. Consider the different types of cold storage solutions available and choose the one that best suits your needs. Remember to follow best practices and stay informed to ensure the safety of your cryptocurrency investments.
Securely Managing Cryptocurrency Transactions
When it comes to managing your cryptocurrency transactions, security should be your top priority. With the digital nature of cryptocurrencies, it is essential to take necessary measures to protect your assets from potential threats. Here are some essential security measures to ensure the safety of your cryptocurrency transactions:
1. Choose a Secure Wallet
Selecting a reputable and secure digital wallet is the first step in managing your cryptocurrency transactions securely. Look for wallets that offer robust security features, such as two-factor authentication and encryption, to protect your digital assets.
2. Use Strong Passwords

Creating strong and unique passwords for your cryptocurrency accounts is crucial. Avoid using common phrases or easily guessable patterns. Opt for a combination of uppercase and lowercase letters, numbers, and special characters to enhance the password security.
3. Enable Two-Factor Authentication (2FA)
Two-factor authentication adds an extra layer of protection to your cryptocurrency transactions. By enabling 2FA, you will need to provide a second verification method, such as a unique code sent to your mobile device, in addition to your password.
4. Be Wary of Phishing Attempts
Be cautious of phishing attempts where cybercriminals try to trick you into revealing your wallet credentials. Avoid clicking on suspicious links or providing personal information on untrusted websites. Always verify the website’s authenticity before entering any sensitive information.
5. Regularly Update Your Wallet Software
Staying up to date with the latest wallet software updates is essential for maintaining the security of your cryptocurrency transactions. Wallet developers often release updates that address security vulnerabilities and provide enhanced protection against potential threats.
6. Keep Your Private Keys Secure
Private keys are crucial for accessing your cryptocurrencies. It is vital to keep them secure and never share them with anyone. Consider storing them offline in an encrypted format or using hardware wallets that provide an extra layer of protection.
7. Employ Cold Storage for Large Amounts
If you’re holding a significant amount of cryptocurrency, consider using cold storage solutions, such as hardware wallets or paper wallets. Cold storage keeps your private keys offline, minimizing the risk of online threats.
8. Backup Your Wallet
Regularly backup your wallet and store the backup in a secure location. A wallet backup ensures that you can regain access to your funds in case of device failure or loss. Consider using encrypted storage or cloud backup services for an added layer of protection.
9. Be vigilant with Third-party Services
When using third-party services for cryptocurrency transactions, such as exchanges or online wallets, ensure they have robust security measures in place. Research their reputation, read reviews, and verify their security protocols before using their services.
10. Educate Yourself on Blockchain Security

Stay informed about the latest developments and best practices in blockchain security. By educating yourself, you will be better equipped to make informed decisions and protect your digital assets.
Implementing these security measures will help safeguard your cryptocurrency transactions and protect your digital assets from potential threats. Remember, the safety of your crypto holdings ultimately rests in your hands, so always prioritize security.
Understanding the Risks of Phishing Attacks
When it comes to protecting your cryptocurrency, one of the most important security measures is understanding the risks of phishing attacks. Phishing attacks are a common tactic used by cybercriminals to trick individuals into revealing sensitive information or login credentials.
What is a phishing attack?
A phishing attack is a type of cyber attack where the attacker poses as a trustworthy entity, such as a bank or a popular cryptocurrency exchange, and attempts to deceive individuals into providing sensitive information. This could include passwords, private keys, or even wallet addresses.
How do phishing attacks work?
Phishing attacks usually start with a fraudulent email, text message, or even a social media post that appears to come from a legitimate source. The message will often contain a sense of urgency, urging the recipient to take immediate action.
The message may include a link to a fake website that is designed to look like a legitimate one. Once the recipient clicks on the link and enters their sensitive information, the attacker will have access to their cryptocurrency assets.
Protecting yourself from phishing attacks
Protecting yourself from phishing attacks requires vigilance and awareness. Here are some essential security measures to keep in mind:
- Be cautious of unsolicited emails and messages: Never click on links or download attachments from unknown sources, especially if they are asking for your login credentials.
- Double-check the website’s URL: Before entering any sensitive information, make sure you are on the correct website. Check for misspellings or variations in the URL that may indicate a fake site.
- Enable two-factor authentication (2FA): By enabling 2FA, you add an extra layer of security to your cryptocurrency accounts. This typically involves entering a code or approving a login attempt through a separate device.
- Keep your software up to date: Regularly update your operating system, web browser, and antivirus software to stay protected against the latest phishing techniques.
Conclusion
Understanding the risks of phishing attacks is essential for the safety and security of your cryptocurrency assets. By being aware of the tactics used by attackers and following proper security measures, you can minimize the risk of falling victim to phishing attacks and protect your digital assets on the blockchain.
Protecting Against Malware and Viruses
- Use reliable antivirus software: Install and regularly update reputable antivirus software to protect your computer and digital assets from malware and viruses.
- Keep your software up to date: Ensure that your operating system, browser, and other software are always updated with the latest security patches. Many malware and virus attacks target vulnerabilities in outdated software.
- Avoid suspicious links and downloads: Be cautious when clicking on links or downloading files from unknown or untrusted sources. These can often contain malware or viruses that can compromise the security of your cryptocurrency assets.
- Enable two-factor authentication (2FA): Use two-factor authentication wherever possible to add an extra layer of security to your crypto accounts. This will require you to provide additional verification, such as a security code sent to your mobile device, before accessing your accounts.
- Secure your crypto wallets: Use hardware wallets or software wallets with strong security features to store your digital assets. Make sure to choose wallets from reputable providers and keep them updated with the latest security patches.
- Regularly back up your data: Create backups of your crypto wallets and other important data regularly. Store these backups in secure locations, such as encrypted external hard drives or offline storage devices.
- Be cautious with public Wi-Fi: Avoid using public Wi-Fi networks when accessing your crypto accounts or making transactions. These networks are often insecure and can be easily compromised by hackers.
- Avoid sharing personal information online: Be mindful of the information you share online, especially on social media platforms. Avoid sharing details about your cryptocurrency holdings or financial transactions, as this can make you a target for hackers.
- Stay informed about the latest threats: Keep yourself updated on the latest security threats and best practices for protecting your cryptocurrency assets. Follow reputable sources, join online security communities, and educate yourself about potential risks.
Being Mindful of Public Wi-Fi Risks
When it comes to the safety and security of your cryptocurrency assets, being mindful of public Wi-Fi risks is crucial. Public Wi-Fi networks are often unsecured and can leave your personal information vulnerable to hackers and cybercriminals.
Given that the blockchain technology and security are the cornerstones of digital assets and cryptocurrencies, it is important to take proper precautions to protect your investments.
The Dangers of Public Wi-Fi Networks
Public Wi-Fi networks are popular targets for hackers because they are typically not secured and are accessible to anyone within range. This makes it easier for cybercriminals to intercept sensitive information, such as passwords, private keys, and other important data.
Once a hacker gains access to your device or network, they can steal your cryptocurrency, gain unauthorized access to your accounts, and potentially even compromise your identity.
Protecting Your Cryptocurrency Assets
To safeguard your digital assets and protect your cryptocurrency investments, it is important to be aware of the risks associated with public Wi-Fi networks and take the necessary precautions:
- Use a VPN: A Virtual Private Network (VPN) encrypts your internet connection and protects your data from being intercepted by hackers on public Wi-Fi networks.
- Avoid Transacting on Public Wi-Fi: Avoid conducting any cryptocurrency transactions or accessing sensitive accounts while connected to a public Wi-Fi network. Wait until you have a secure and trusted internet connection.
- Use Two-Factor Authentication: Enable two-factor authentication (2FA) on all your cryptocurrency accounts. This adds an extra layer of security by requiring a second verification step, such as a code sent to your mobile device, in addition to your password.
- Keep Software Updated: Regularly update your devices’ software, including your operating system and antivirus software, to ensure you have the latest security patches.
Conclusion
Protecting your cryptocurrency investments requires being mindful of the potential risks associated with public Wi-Fi networks. By using a VPN, avoiding transactions on public Wi-Fi, enabling two-factor authentication, and keeping your software updated, you can greatly enhance the security of your digital assets.
Remember, the safety and security of your cryptocurrency holdings rely on your proactive measures to protect them from potential threats.
Ensuring the Security of Your Cryptocurrency Investments
When it comes to digital assets and cryptocurrencies, security should be your top priority. Protecting your investment is essential, considering the high value and potential risks associated with this new form of currency.
Understanding the Importance of Security
As cryptocurrencies are based on the blockchain technology, they offer a high level of security. However, it is important to take additional measures to ensure the safety of your cryptocurrency
Essential Security Measures
- Wallet Security: Use a trusted and reputable digital wallet to store your cryptocurrency, preferably one that provides offline storage and multi-factor authentication.
- Strong Passwords: Create a strong and unique password for your wallet and any other accounts related to your cryptocurrency investments.
- Two-Factor Authentication: Enable two-factor authentication (2FA) whenever possible to add an extra layer of security to your accounts. This typically involves entering a unique code generated on your smartphone or other device.
- Phishing awareness: Be cautious of phishing attempts, where hackers may pose as legitimate entities to obtain your personal information. Always double-check the URL and ensure the website is secure before entering any sensitive information.
- Secure Internet Connection: Use a secure and private internet connection whenever accessing your cryptocurrency accounts or making transactions. Avoid using public Wi-Fi networks.
- Regular Updates: Keep your wallet software and any other related applications up to date to benefit from the latest security enhancements.
- Backup Your Wallet: Regularly backup your wallet and store the backup in a secure location. This ensures that even if your device is lost or stolen, you can still access your funds.
- Secure Storage: If you choose to store your cryptocurrency on a hardware wallet, ensure it is kept in a secure physical location, such as a safe or locked drawer.
Seek Professional Advice
Consider seeking advice from a cryptocurrency security professional to ensure you are taking all the necessary steps to protect your digital assets adequately. These experts can offer insights into the latest security practices and help you identify potential vulnerabilities in your security measures.
Conclusion
Protecting your cryptocurrency investments is crucial in today’s digital landscape. By implementing the essential security measures mentioned above and staying vigilant, you can reduce the risks and ensure the safety of your valuable digital assets.
Seeking Professional Advice on Digital Asset Protection
Protecting your cryptocurrency is crucial in today’s digital age. With advancements in technology and the rise of blockchain, digital assets have become valuable and sought-after targets for hackers. To ensure the safety and security of your assets, seeking professional advice on digital asset protection is highly recommended.
Why Seek Professional Advice?
- Expertise: Professionals in the field of digital asset protection have the necessary knowledge and experience to safeguard your assets. They understand the complexities of the crypto world and can provide guidance based on the latest industry best practices.
- Threat Analysis: Professionals can conduct a thorough analysis of potential threats and vulnerabilities specific to your digital assets. This helps in identifying potential risks and developing effective security measures to mitigate them.
- Cutting-Edge Solutions: Professionals stay updated with the latest advancements in digital asset protection. They can recommend and implement state-of-the-art security solutions, such as multi-factor authentication, hardware wallets, and cold storage, to ensure the highest level of protection for your assets.
- Customized Approach: Each individual or organization has unique security requirements. Professional advisors can tailor their recommendations to suit your specific needs, taking into account factors like the size of your asset portfolio, the level of risk tolerance, and regulatory compliance.
Choosing a Professional Advisor
When seeking professional advice on digital asset protection, consider the following:
- Experience and Reputation: Look for advisors who have a proven track record of working in the field of digital asset security. Check for certifications, testimonials, and reviews to assess their expertise and reputation.
- Industry Knowledge: Digital asset security is a rapidly evolving field. Ensure that the advisor you choose is up to date with the latest trends, regulations, and technologies.
- Clear Communication: The advisor should be able to explain complex concepts and security measures in clear and concise terms. Effective communication is essential for understanding and implementing their recommendations.
- Cost and Fees: Understand the cost structure and fees associated with their services. Ensure that the value they provide aligns with the fees charged.
Conclusion
Protecting your cryptocurrency and other digital assets requires a proactive approach. Seeking professional advice on digital asset protection is a smart move to ensure the security, safety, and longevity of your investments. By working with experts in the field, you can stay one step ahead of potential threats and keep your assets secure in the fast-paced world of cryptocurrency and blockchain.
Frequently asked questions:
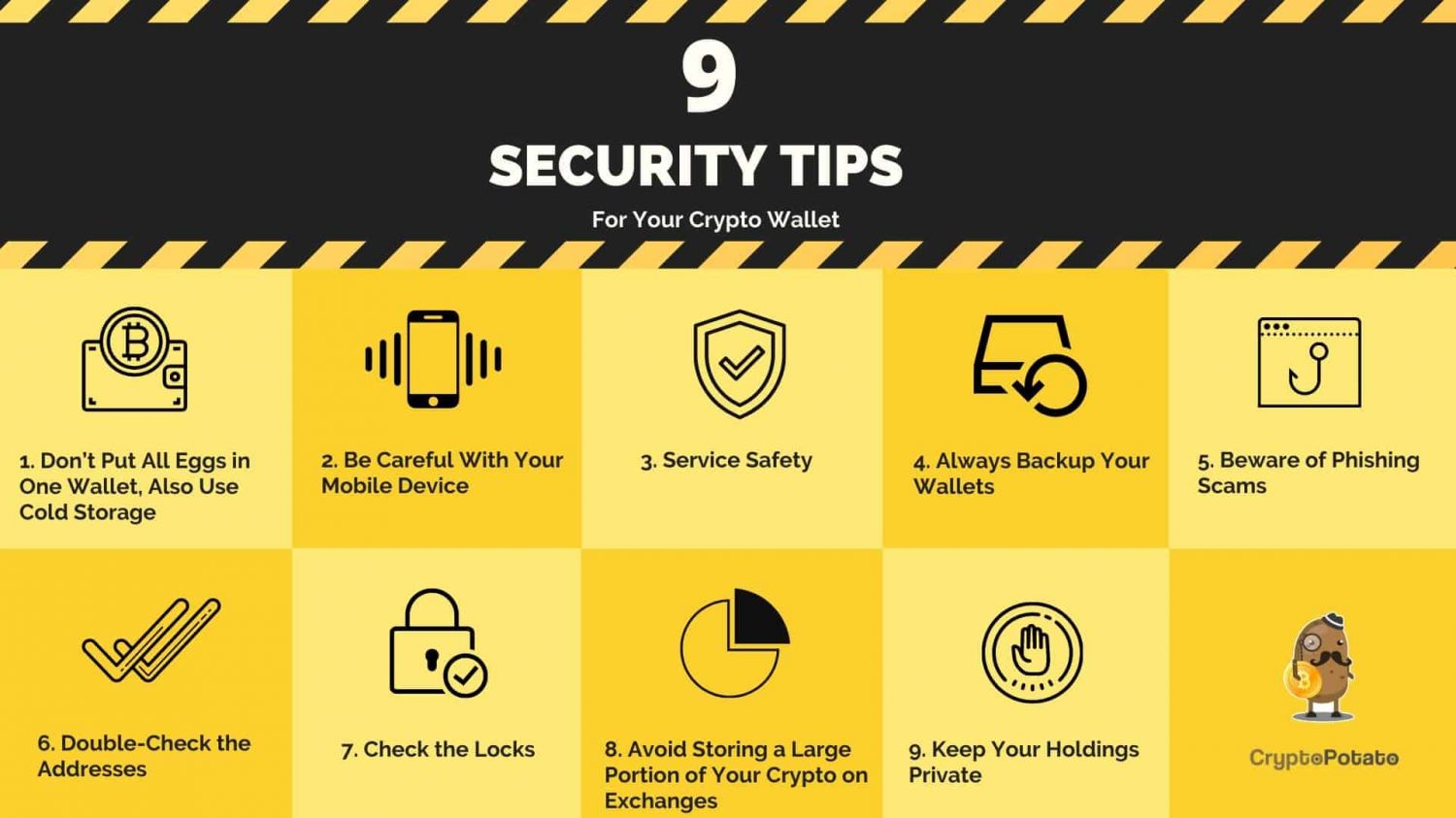
What are the essential security measures to protect my cryptocurrency?
There are several essential security measures to protect your cryptocurrency. Firstly, it is important to use a strong and unique password for your cryptocurrency wallet. Additionally, enabling two-factor authentication adds an extra layer of security. It is also crucial to keep your software and devices up to date with the latest security patches. Lastly, storing your cryptocurrency offline in a hardware wallet or a paper wallet can provide an extra level of protection against online threats.
How can I secure my digital assets on the blockchain?
Securing digital assets on the blockchain involves several measures. One important step is to choose a secure and reputable cryptocurrency wallet to store your assets. It is also essential to keep your private key secure and not share it with anyone. Enabling two-factor authentication and using strong passwords for your wallet are additional security measures. Regularly monitoring your transactions and verifying the security measures of the blockchain platform you are using can also help protect your digital assets.
What are some common security risks associated with cryptocurrency?
There are several common security risks associated with cryptocurrency. One risk is the possibility of a cyber attack or hacker gaining unauthorized access to your wallet or digital assets. Phishing attacks, where scammers trick users into revealing their private keys or login credentials, are also a common risk. Another potential risk is the vulnerability of cryptocurrency exchanges to hacking or insider threats. Additionally, the risk of malware or viruses targeting cryptocurrency wallets or devices is a concern.
Is it safe to store cryptocurrency on an exchange?
Storing cryptocurrency on an exchange carries some level of risk. While reputable exchanges implement security measures to protect user accounts and assets, there is always a possibility of a security breach. Hackers may target exchanges to gain access to user funds. It is generally considered safer to store cryptocurrency in a personal wallet where the user has full control over their private keys. However, if choosing to store cryptocurrency on an exchange, it is important to research and select a reputable and secure platform.
What is a hardware wallet and why is it considered secure?
A hardware wallet is a physical device designed to securely store cryptocurrency offline. It is considered secure because the private keys necessary for accessing the cryptocurrency are stored on the device itself, rather than on a computer or online platform. This means that even if a computer or online wallet is compromised, the private keys remain safe. Hardware wallets also typically require a physical button press or other authentication methods to authorize transactions, adding an extra layer of security.
What should I do if my cryptocurrency wallet is hacked?
If your cryptocurrency wallet is hacked, it is important to act quickly to minimize the potential damage. First, disconnect the compromised device from the internet to prevent further unauthorized access. Change any passwords associated with the hacked wallet and enable two-factor authentication if it wasn’t already enabled. Report the incident to the wallet provider and any relevant authorities. Consider transferring your remaining funds to a new, secure wallet. It may also be necessary to scan your device for malware or viruses that could have allowed the hack to occur.
Videos:
Protect Your Crypto: A Beginner’s Guide

I have been investing in cryptocurrency for a while now, and I can’t stress enough the importance of taking security measures. With the increasing risks of theft and breaches, it’s crucial to protect your digital assets. Storing your cryptocurrency in a secure digital wallet and using strong passwords are simple yet effective ways to ensure the safety of your investments. Don’t overlook these essential security measures!
I completely agree with the article. Protecting your cryptocurrency should be a top priority for every investor. I’ve been using blockchain technology for a while now and it has proven to be incredibly secure. Storing my digital assets in a secure digital wallet has also given me peace of mind. It’s important to stay vigilant and take all necessary security measures to keep your investments safe.
I completely agree with the importance of taking extra security measures to protect our cryptocurrency. The rising popularity of digital assets has also attracted more hackers and thieves. Storing our cryptocurrency in a secure digital wallet and using strong, unique passwords are crucial to safeguard our investments. It’s better to be safe than sorry!
Protecting your cryptocurrency is of utmost importance in this digital era. The blockchain technology is a game-changer when it comes to security, but it’s not enough. Storing your digital assets in a secure digital wallet and using strong passwords are necessary precautions to keep your investments safe. Stay vigilant!
I totally agree with the importance of taking necessary security measures to protect our cryptocurrency. With the advancements in technology, we must be extra cautious in safeguarding our digital assets. Storing our cryptocurrency in a secure digital wallet and using strong passwords are just some of the ways we can ensure the safety of our investments.
I completely agree with the importance of securing cryptocurrency assets. As a cryptocurrency enthusiast, I always make sure to store my digital assets in a secure wallet and use strong passwords for all my accounts. Safety is crucial in this new digital era!
How often should I update my wallet software to stay secure?
Regularly updating your wallet software is crucial to maintaining the security of your cryptocurrency. As new vulnerabilities and security threats are identified, developers release updates to fix these issues and enhance the overall security of the software.
Could you explain more about how digital wallets work and the different options available? I want to make sure I choose the most secure one for my cryptocurrency.
Sure, Chloe2187! Digital wallets are applications or devices that allow you to securely store and manage your cryptocurrency. They work by generating and storing private and public keys, which are used to access and sign transactions on the blockchain. There are several options available for digital wallets, including hardware wallets, which store your keys offline on a physical device, and software wallets, which are applications that run on your computer or smartphone. Both options have their advantages and it’s important to choose one that fits your needs and provides strong security measures. Researching and comparing different wallet providers is a good practice to ensure you select the most secure one for your cryptocurrency. Stay safe!
Are there any other security measures I should consider besides storing my cryptocurrency in a digital wallet and using strong passwords?
Absolutely, John_Smith278! Besides storing your cryptocurrency in a digital wallet and using strong passwords, you should also enable two-factor authentication (2FA) for your cryptocurrency accounts. 2FA adds an extra layer of security by requiring a second form of verification, such as a code sent to your mobile device, in addition to your password. This makes it much harder for hackers to gain unauthorized access to your accounts. It’s also important to keep your wallet software and antivirus software up to date, as these updates often include security patches that address any vulnerabilities. Stay vigilant and be cautious of phishing attempts or suspicious links. Remember, the more steps you take to secure your cryptocurrency, the better protected you’ll be. Happy investing!
Can you recommend any trusted digital wallets for storing cryptocurrency securely?
Sure, crypto_enthusiast! When it comes to storing your cryptocurrency securely, there are several trusted digital wallet options available. One popular choice is “SecureVault”, which offers high-level encryption and multi-factor authentication to protect your digital assets. Another reliable option is “FortifyWallet”, known for its user-friendly interface and robust security features. Make sure to do your own research and choose a wallet that fits your needs and preferences. Stay safe!
Is it really necessary to use a digital wallet for cryptocurrency storage? Can’t I just keep it on the exchange platform?
Yes, it is highly recommended to use a digital wallet for cryptocurrency storage. While exchange platforms may offer some level of security, they are still susceptible to hacking and breaches. By using a digital wallet, you have full control and ownership of your private keys, which are necessary for accessing and transferring your cryptocurrency. This adds an extra layer of security to your digital assets. Keep in mind that not all digital wallets are created equal, so be sure to choose a reputable and highly secure wallet.
I completely agree with the article. Protecting your cryptocurrency is of utmost importance in today’s digital world. As a crypto investor myself, I always make sure to use strong and unique passwords for all my cryptocurrency accounts. I also opt for secure digital wallets to store my digital assets. It’s crucial to stay one step ahead of potential hackers and ensure the safety of our investments.
What are some other security measures that can be taken to protect cryptocurrency?
One of the additional security measures that can be taken to protect cryptocurrency is to enable two-factor authentication (2FA) for all your cryptocurrency accounts. 2FA adds an extra layer of security by requiring a second form of authentication, such as a unique code sent to your mobile device, in addition to your password. This helps to prevent unauthorized access even if your password is compromised.
Are there any specific digital wallets you would recommend for storing cryptocurrency securely?
Sure, AlexB82! When it comes to storing your cryptocurrency securely, there are a few digital wallets that are highly recommended. One popular option is Ledger Nano S, which is a hardware wallet that provides an extra layer of security by keeping your private keys offline. Another good choice is Trezor, which also offers a hardware solution to store your cryptocurrency safely. Both wallets have a strong reputation for their security features and user-friendly interface. Remember to do thorough research before choosing a wallet and always keep your wallet software updated to ensure maximum security.
As a cryptocurrency investor, I fully agree with the importance of taking security measures to protect our digital assets. It’s crucial to use strong and unique passwords for all our crypto accounts. Additionally, storing our cryptocurrency in a secure digital wallet adds an extra layer of protection. Let’s stay proactive in safeguarding our investments in the digital realm!
I completely agree with the importance of protecting your cryptocurrency. With the increasing popularity of digital assets, it’s crucial to take security measures seriously. Storing your cryptocurrency in a secure digital wallet and using strong and unique passwords are essential steps to safeguarding your investments. The blockchain technology provides a foundation of security, but it’s always better to be safe than sorry.
Can you provide some examples of secure digital wallets for cryptocurrency storage?
Sure! When it comes to secure digital wallets for cryptocurrency storage, there are several options to consider. Some popular choices include Ledger Nano S, Trezor Model T, and Coinbase Wallet. These wallets are known for their high level of security and encryption, providing a safe and reliable way to store your digital assets. Additionally, they often offer features such as multi-factor authentication and offline storage to further enhance the protection of your cryptocurrency. I would recommend researching each option and choosing the one that best fits your needs and preferences.
Protecting your cryptocurrency is crucial in today’s digital age. With the increasing risks of theft and security breaches, it is essential to take extra security measures. Storing your digital assets in a secure digital wallet and using strong, unique passwords for all your accounts are key steps to safeguarding your investments.
I completely agree with the article. The security of our cryptocurrency should be a top priority for all investors. Storing it in a secure digital wallet and using strong passwords are simple yet effective measures to protect our valuable assets. We cannot afford to be complacent when it comes to the safety of our investments.
I completely agree with the importance of taking strong security measures to protect your cryptocurrency. With the increasing risks of theft and security breaches, it’s crucial to store your digital assets in a secure wallet and use strong passwords to ensure their safety.
As a seasoned cryptocurrency enthusiast, I cannot stress enough the importance of implementing strong security measures to safeguard your digital assets. With the blockchain technology in place, we have a solid foundation for security, but it is crucial to also utilize secure digital wallets and unique passwords for added protection.
Is it necessary to use different passwords for every cryptocurrency account?
Yes, it is absolutely necessary to use different passwords for every cryptocurrency account. Using the same password for multiple accounts increases the risk of a potential security breach. If one account is compromised, all your other accounts would be vulnerable as well. By using unique passwords, you add an extra layer of security to each individual account, making it much harder for hackers to gain unauthorized access.
I totally agree with the article. The rise of cryptocurrency means that we need to be extra cautious with our digital assets. Storing cryptocurrency in secure digital wallets and using strong passwords are essential security measures that we should all take. It’s better to be safe than sorry!
What are some other security measures that can be taken to protect cryptocurrency?
Hi Alexander, there are several other security measures you can take to protect your cryptocurrency. One important measure is to enable two-factor authentication on your cryptocurrency accounts. This adds an extra layer of security by requiring a second form of verification, such as a code sent to your phone, in addition to your password. Additionally, it is crucial to keep your devices and software up to date with the latest security patches and updates. This reduces the risk of vulnerabilities that could be exploited by hackers. Lastly, be cautious of phishing attempts and only access your cryptocurrency accounts through official and trusted platforms. Stay safe!
I completely agree with the importance of taking additional security measures to protect our cryptocurrency. As someone who has invested a substantial amount in digital assets, I always make sure to use strong and unique passwords for all my cryptocurrency accounts. It adds an extra layer of security and helps me feel more confident about the safety of my investments.
I completely agree with the article. As someone who has been in the cryptocurrency market for quite some time, I can attest to the importance of taking security measures seriously. Using a digital wallet and strong passwords are essential for protecting your assets. The blockchain technology may offer some security, but it’s always better to be safe than sorry.
I totally agree with the importance of taking extra security measures to protect your cryptocurrency. With the increasing risks of theft and security breaches, it’s crucial to safeguard our valuable digital assets. Storing our cryptocurrency in a secure digital wallet and using strong, unique passwords for our accounts are among the essential steps to ensure the safety of our investments.
Great article! It’s crucial to prioritize the security of our cryptocurrency investments. Storing them in a secure digital wallet and using strong passwords are definitely essential measures to protect our digital assets. Thanks for the informative read!
Are there any specific digital wallets that you recommend for storing cryptocurrency securely?
Sure, JamesBond007! When it comes to digital wallets for storing cryptocurrency securely, there are several options to consider. One popular choice is the Ledger Nano S, which is a hardware wallet that offers offline storage and strong security features. Another option is the Exodus wallet, which is a software wallet that provides a user-friendly interface and supports multiple cryptocurrencies. Additionally, the Trezor wallet is also highly recommended for its advanced security features. These wallets offer different features and levels of security, so it’s important to research and choose the one that best suits your needs. Remember to always verify the legitimacy of the wallet provider and regularly update your wallet software to ensure maximum security for your digital assets!
Is it safe to store my cryptocurrency in a digital wallet? Are there any risks involved?
Yes, it is generally safe to store your cryptocurrency in a digital wallet. Digital wallets provide a secure and encrypted environment to hold your digital assets. However, there are some risks involved that you should be aware of. Firstly, make sure that you choose a reputable and reliable digital wallet service to minimize the risk of a security breach. Additionally, always keep your wallet software and mobile device up to date with the latest security patches. Lastly, it’s crucial to implement strong security measures such as two-factor authentication and biometric authentication to further enhance the safety of your cryptocurrency stored in a digital wallet.
How can I choose a secure digital wallet? Are there any recommendations?
Choosing a secure digital wallet for your cryptocurrency is a crucial step in protecting your digital assets. Here are some recommendations:
1. Research and read reviews: Before selecting a digital wallet, it’s important to research and read reviews from reputable sources. This will help you get an idea of the wallet’s security features and any potential vulnerabilities.
2. Look for wallet encryption: Make sure the wallet you choose has encryption features that protect your private keys. This adds an extra layer of security to your digital assets.
3. Check for multi-factor authentication: Opt for a digital wallet that offers multi-factor authentication. This means you’ll need to provide additional verification, such as a fingerprint or a unique code sent to your phone, in order to access your wallet.
4. Offline storage options: Consider a digital wallet that offers offline storage options, such as hardware wallets or paper wallets. These wallets store your private keys offline, making them less vulnerable to online attacks.
5. Trusted developers: Choose a digital wallet developed by trusted and reputable developers. Look for wallets that have a strong track record and a large user base.
Remember, the security of your cryptocurrency ultimately falls on your shoulders. Stay informed, keep your software updated, and be cautious when interacting with unknown sources online. With the right security measures in place, you can protect your valuable digital assets from potential threats.
I completely agree with this article. As a cryptocurrency investor, I understand the importance of protecting my digital assets. Blockchain technology provides a strong foundation for security, but it’s crucial to take extra measures such as using secure digital wallets and strong passwords. Safety should always be a top priority in the crypto world.
I completely agree with the importance of taking extra security measures to protect your cryptocurrency. It’s crucial to store your digital assets in a secure digital wallet and use strong, unique passwords for your accounts. With the rise in theft and security breaches, it’s better to be safe than sorry.
As an avid crypto investor, I couldn’t agree more with the importance of taking necessary security measures to protect our digital assets. The blockchain technology indeed offers a high level of security, but having a secure digital wallet and strong passwords are essential to safeguard our investments and keep the hackers at bay.
I totally agree with this article. The security of our cryptocurrency is crucial, especially in this digital age where hackers are becoming more sophisticated. Storing our digital assets in a secure wallet and using strong passwords are some of the basic steps we can take to protect our investments. Let’s not forget that prevention is always better than cure.
Is it necessary to use a different password for each cryptocurrency account?
Yes, it is absolutely necessary to use a different password for each cryptocurrency account. Using the same password across multiple accounts increases the risk of a security breach. If one account is compromised, hackers can easily gain access to all your other accounts. By using strong and unique passwords for each account, you significantly reduce the chances of your cryptocurrency being stolen or hacked. Remember, the security of your digital assets should always be a top priority.
I completely agree with the importance of taking additional security measures to protect your cryptocurrency. It’s crucial to have a secure digital wallet and strong passwords for all your accounts. The rise of blockchain technology has definitely improved security in the crypto world, but hackers are always finding new ways to exploit vulnerabilities. Better safe than sorry!
Can you recommend any specific digital wallets for storing cryptocurrency securely?
Of course, I can help you with that! When it comes to digital wallets for storing cryptocurrency securely, I would recommend considering hardware wallets like Ledger Nano X or Trezor Model T. These wallets offer enhanced security features such as offline storage and multi-factor authentication, making it harder for hackers to gain unauthorized access to your funds. Additionally, they support a wide range of cryptocurrencies, providing you with flexibility in managing your digital assets. Stay safe and protect your investments!
Cryptocurrency security is of utmost importance in today’s digital world. It’s crucial to follow best practices to protect our digital assets. Storing our currency in a secure digital wallet and using strong passwords are simple steps we can take to safeguard our investments.
Could you provide more information on how to choose a secure digital wallet for storing cryptocurrency?
Sure, selecting a secure digital wallet for your cryptocurrency is crucial in safeguarding your assets. When choosing a digital wallet, opt for reputable providers that offer features like multi-factor authentication, biometric security, and encryption protocols. It’s also advisable to research and read reviews to ensure the wallet has a strong track record of security and reliability. Remember, protecting your private keys and ensuring the wallet is regularly updated are essential steps in enhancing the security of your cryptocurrency holdings.
How can I ensure that my digital wallet is truly secure against potential hacking attempts?
To ensure that your digital wallet is truly secure against potential hacking attempts, make sure to enable two-factor authentication (2FA) for an added layer of security. Additionally, regularly update your wallet software to patch any vulnerabilities that could be exploited by hackers. Stay vigilant and avoid sharing your wallet credentials with anyone to keep your digital assets safe.
As a cryptocurrency enthusiast myself, I couldn’t agree more with the importance of robust security measures for protecting digital assets. It’s crucial to stay vigilant and implement best practices like secure digital wallets and strong passwords to safeguard our investments in the volatile world of cryptocurrency.
In today’s digital age, protecting your cryptocurrency is crucial to safeguarding your investments in the volatile world of digital assets. As a cryptocurrency investor, it’s important to stay informed about the latest security measures and technologies that can help mitigate the risks of theft and security breaches. By utilizing blockchain technology and adopting secure practices like storing your assets in digital wallets and using strong passwords, you can enhance the security of your cryptocurrency holdings and protect them from malicious actors.
How can I ensure that my digital wallet is truly secure and protected from potential hacks?
To ensure that your digital wallet is truly secure and protected from potential hacks, it’s crucial to choose a reputable and trusted digital wallet provider that offers robust security features such as two-factor authentication, encryption, and backup options. Additionally, regularly updating your wallet software, enabling security settings, and being cautious of phishing attempts can further enhance the security of your digital assets.
Protecting my cryptocurrency is crucial in today’s digital world. I believe that utilizing secure digital wallets and employing strong, unique passwords are essential steps to safeguard my valuable digital assets. It’s reassuring to know that blockchain technology provides a decentralized and transparent ledger, enhancing the security of my transactions.
In my opinion, safeguarding your cryptocurrency is crucial in today’s digital landscape. With the increasing risks of security breaches, it’s essential to utilize advanced technologies like blockchain to ensure the safety of your digital assets. Additionally, using secure digital wallets and creating strong passwords are key measures to protect your valuable investments in the cryptocurrency realm.
Could you provide more insights on the types of digital wallets recommended for storing cryptocurrency securely?
Sure, EmmaSmith92! When it comes to storing your cryptocurrency securely, hardware wallets and paper wallets are highly recommended. Hardware wallets are physical devices that store your private keys offline, making them less vulnerable to hacking attempts. Paper wallets, on the other hand, involve printing out your private keys and storing them in a secure place offline. Both options provide an extra layer of security compared to online wallets. Remember, always research and choose reputable wallet providers to safeguard your digital assets.
As a cryptocurrency enthusiast, I believe that safeguarding our digital assets should be a top priority. Blockchain technology provides a strong foundation for security, but additional measures like secure wallets and robust passwords are essential to protect our investments.
How effective are digital wallets in protecting against theft compared to other security measures mentioned in the article?
Hi EthanCrypto, digital wallets play a crucial role in protecting your cryptocurrency assets. They provide an added layer of security by storing your digital assets in a secure and encrypted environment, making it harder for hackers to access your funds. While strong passwords and best practices are vital, using a digital wallet adds an extra level of protection against theft. It’s always recommended to combine multiple security measures to safeguard your investments in the world of cryptocurrency.
In today’s digital age, cryptocurrency has become a popular investment and a store of value. I believe that safeguarding our investments in the world of cryptocurrency is crucial. The blockchain technology indeed provides a layer of security, but implementing additional measures like using secure digital wallets and strong passwords is essential to protect our valuable digital assets.
How can I ensure that my digital wallet is truly secure against potential breaches?
To ensure that your digital wallet is truly secure against potential breaches, make sure to choose a reputable wallet provider with a track record of security. Enable two-factor authentication and regularly update your wallet software to patch any vulnerabilities. Additionally, consider using a hardware wallet for added security measures.
Protecting your cryptocurrency is crucial in today’s digital landscape. The blockchain technology offers a secure foundation, but additional measures such as utilizing secure digital wallets and strong passwords are essential for safeguarding your valuable assets.
How can I ensure that my digital wallet is truly secure? Are there specific features I should look for?
To ensure that your digital wallet is truly secure, look for features such as multi-factor authentication, encryption of private keys, and compatibility with hardware wallets. These elements enhance the security of your cryptocurrency holdings and protect them from potential threats.
In today’s digital age, safeguarding your cryptocurrency is crucial. As a cryptocurrency investor myself, I believe utilizing strong security measures, such as secure digital wallets and unique passwords, is vital to protecting our valuable digital assets from potential theft or unauthorized access. Let’s all stay vigilant in ensuring the safety of our investments in the world of cryptocurrency.
As someone deeply involved in the world of cryptocurrency, I cannot stress enough the importance of implementing robust security measures to protect your digital assets. Blockchain technology provides a strong foundation for security, but individual responsibility in using secure wallets and unique passwords is crucial in safeguarding your investments in this volatile market.
How can I ensure the security of my cryptocurrency investments when there are risks of theft and security breaches?
To enhance the security of your cryptocurrency investments in the face of potential theft and security breaches, consider utilizing hardware wallets for added protection. These physical devices store your crypto offline, making it nearly impossible for hackers to breach your assets remotely.
Protecting my cryptocurrency is crucial to me. I believe that utilizing advanced security measures, such as secure digital wallets and strong, unique passwords, is essential in safeguarding my valuable digital assets. The transparency of blockchain technology definitely adds an extra layer of security, but proactive measures are still necessary to mitigate risks.
Protecting your cryptocurrency is crucial in today’s digital age. The blockchain technology offers inherent security, but it’s vital to implement additional measures like using secure digital wallets and strong, unique passwords to safeguard your valuable digital assets.
In today’s digital age, cryptocurrency has become a popular investment and a store of value. However, with the rise of this new form of digital asset, there are also increased risks of theft and security breaches. Ensuring the safety and protection of your cryptocurrency is paramount in order to safeguard your valuable digital assets.
As a cryptocurrency investor, I believe that protecting our digital assets is crucial in today’s digital landscape. The advancement of blockchain technology has provided a certain level of security, but it’s vital for individuals to implement additional measures like secure digital wallets and strong passwords to safeguard their investments.
How can I ensure that my digital wallet is truly secure and immune to hacking attempts?
To enhance the security of your digital wallet, make sure to choose a reputable wallet provider with a track record of strong security measures. Additionally, enable two-factor authentication for an added layer of protection against unauthorized access attempts. Regularly update your wallet software and avoid sharing sensitive information online to minimize the risk of hacking incidents.
How can I ensure that my digital wallet is truly secure from potential theft?
To ensure that your digital wallet is truly secure from potential theft, make sure to choose a reputable wallet provider with a strong track record of security. Additionally, enable two-factor authentication and regularly update your wallet software to protect against any vulnerabilities. Stay vigilant and avoid sharing your private keys or sensitive information with anyone. Remember, proactive measures are key to safeguarding your cryptocurrency investments.
In today’s digital age, cryptocurrency has become a popular investment and a store of value. However, with the rise of this new form of digital asset, there are also increased risks of theft and security breaches. Ensuring the safety and protection of your cryptocurrency is paramount in order to safeguard your valuable digital assets. One of the main reasons why cryptocurrency is considered to be more secure than traditional forms of currency is because it operates on blockchain technology. The blockchain is a decentralized and transparent ledger that records all transactions made with a particular cryptocurrency. This means that every transaction is verified by multiple participants in the network, making it extremely difficult for hackers to tamper with or corrupt the data. However, despite the inherent security provided by the blockchain, it is still essential to take additional security measures to protect your cryptocurrency. One such measure is to store your cryptocurrency in a secure digital wallet. Digital wallets are specifically designed to securely store your cryptocurrency and protect it from theft or unauthorized access. Another important security measure is to use strong and unique passwords for all your cryptocurrency accounts.
As a cryptocurrency investor, I fully agree that protecting our digital assets is crucial in today’s digital world. Blockchain technology indeed provides a layer of security, yet implementing additional measures like secure wallets and strong passwords is essential to safeguard our investments.
In today’s digital age, cryptocurrency has become a popular investment and a store of value. It is crucial to protect our digital assets in the world of cryptocurrency by implementing essential security measures. Blockchain technology provides a secure foundation, but additional steps, such as using secure digital wallets and unique passwords, are necessary to safeguard our investments.
Do you have any tips on how to choose the most secure digital wallet for storing cryptocurrency?
Choosing the most secure digital wallet for storing cryptocurrency is crucial. One tip is to opt for wallets that offer two-factor authentication and encryption features to enhance security. Additionally, ensure the wallet has a good reputation in the crypto community and regularly updates its security protocols to stay ahead of potential threats. Researching and comparing different wallet options can help you make an informed decision to protect your digital assets effectively.
Are there any specific digital wallets you recommend for storing cryptocurrency securely? How can I ensure that my passwords are strong enough to protect my digital assets?
Hey SophiaSmith33, when it comes to storing your cryptocurrency securely, popular digital wallets like Ledger Nano S or Trezor are highly recommended for their strong security features. As for ensuring strong passwords, try using a combination of letters, numbers, and special characters, and avoid using easily guessable information like your name or birthdate. Stay safe and keep your digital assets protected!
I believe that taking proactive steps to protect your cryptocurrency is crucial in today’s digital landscape. Safeguarding your digital assets through secure digital wallets and unique passwords is essential to mitigate the risks of theft and unauthorized access. It’s important to stay informed about blockchain security practices to ensure the safety of your investments in the world of cryptocurrency.
In today’s digital age, protecting your cryptocurrency is crucial to ensure the safety of your valuable digital assets. Utilizing blockchain technology provides a layer of security, but it’s also essential to implement additional measures such as secure digital wallets and strong passwords to safeguard your investments in the digital realm.
Protecting your cryptocurrency is crucial in the digital age. As a crypto investor, it’s essential to prioritize security measures to safeguard your digital assets. Utilizing blockchain technology ensures transparency and reduces the risk of hacking attempts. Storing your crypto in a secure digital wallet and using strong passwords are key steps towards enhancing the safety of your investments.
Protecting Your Cryptocurrency is crucial in today’s digital landscape. As a crypto investor, I believe that implementing strong security measures, such as using digital wallets and unique passwords, is imperative to safeguarding our valuable assets in the volatile world of cryptocurrency.
As a crypto enthusiast, I couldn’t agree more with the importance of securing our digital assets. It’s crucial to stay vigilant and implement the necessary security measures to protect our investments in the ever-evolving world of cryptocurrency. Utilizing technologies like blockchain for added security is a step in the right direction, but we must also be proactive in safeguarding our cryptocurrency through secure wallets and strong passwords.
As a cryptocurrency enthusiast, I couldn’t agree more with the importance of prioritizing security measures to protect our digital assets. The blockchain technology is indeed a game-changer in ensuring the integrity of transactions, but additional steps like using secure wallets and strong passwords are crucial to stay ahead of potential risks in the digital realm.
As a cryptocurrency investor, I believe that safeguarding our digital assets is crucial in today’s digital landscape. The blockchain technology provides a solid foundation for security, but implementing additional measures like secure wallets and strong passwords is essential to protect our investments.
Ensuring the safety of your cryptocurrency is crucial in today’s digital landscape. Blockchain technology provides a robust layer of security, but additional measures such as using secure digital wallets and strong passwords are essential to protect your valuable assets from potential threats.
As a cryptocurrency enthusiast, I believe that safeguarding our digital assets is crucial in the volatile world of blockchain technology. The rise in cyber threats emphasizes the need for robust security measures to protect our investments. Storing cryptocurrency in secure wallets and using strong passwords are fundamental steps to ensure the safety of our valuable assets.
As a cryptocurrency enthusiast, I couldn’t agree more with the importance of securing our digital assets. Blockchain technology definitely provides a strong foundation for security, but it’s crucial for us to take proactive steps like utilizing secure digital wallets and implementing robust password practices to safeguard our cryptocurrency investments.
As an avid investor in cryptocurrency, I cannot stress enough the importance of implementing strong security measures to protect our digital assets. The blockchain technology may provide a certain level of security, but it is crucial for us to take proactive steps such as using secure digital wallets and unique passwords to safeguard our investments from potential threats.
As someone who has been investing in cryptocurrency for a while now, I can’t stress enough how critical it is to prioritize security. Using a secure digital wallet and employing strong passwords are non-negotiable steps for anyone serious about their investments. It’s surprising how many people overlook these simple measures, thinking their assets are safe. In this fast-evolving landscape, we must stay informed and vigilant to protect our digital wealth.
I believe protecting your cryptocurrency is absolutely critical in today’s investment landscape. The blockchain offers a strong base, but relying solely on it isn’t enough. I’ve always stressed the importance of using a secure digital wallet and having unique passwords for each account. It’s better to be safe than sorry—no one wants their hard-earned assets lost to cybercriminals!
As someone who has invested in cryptocurrency for over three years, I can’t stress enough how vital it is to take your security seriously. Using a secure digital wallet and strong, unique passwords has saved me from potential hacks. The blockchain may provide a solid foundation for security, but personal vigilance is the key to protecting my investments. Don’t overlook these steps!
I absolutely agree with the emphasis on digital wallets and unique passwords. It’s so important to stay vigilant in this space! With the amount of scams and hacks happening, taking extra precautions really makes a difference. We can’t afford to be complacent when it comes to safeguarding our investments!
What are some recommended practices for creating and managing strong passwords for my digital wallet?
Hi Alexandra! One effective practice is to use a mix of uppercase and lowercase letters, numbers, and special characters. Additionally, consider using a passphrase instead of a single word; it can be a random combination of words or a memorable sentence. Always enable two-factor authentication whenever possible to add an extra layer of security. Stay safe!
I absolutely agree that securing your cryptocurrency should be a top priority. I always use a hardware wallet to store my assets, and I never share my passwords. The blockchain is a great starting point for security, but personal vigilance is key to avoiding theft. It’s a bit overwhelming at times, but with the right practices, we can protect our investments.
It’s so important to take the time to understand cryptocurrency security. I’ve had friends who lost their investments just because they didn’t secure their wallets properly. Using strong passwords and storing crypto in a secure wallet should be the first step for anyone getting into this space. Let’s not underestimate the potential risks!
I believe that protecting our cryptocurrency should be a top priority for anyone investing in digital assets. It’s not enough to rely solely on the blockchain’s security; we need to be proactive. I’ve seen too many friends lose their hard-earned money due to weak passwords and unsecure wallets. Using a reliable digital wallet and updating passwords regularly can make a significant difference in safeguarding our investments. Let’s stay safe out there!
Great article! I’m curious, what specific features should I look for when choosing a secure digital wallet for my cryptocurrency?
Thanks for the question, Jessica! When selecting a secure digital wallet, look for features like two-factor authentication, multi-signature support, and a good reputation within the crypto community. Ensure the wallet allows you full control of your private keys and supports the cryptocurrencies you’re interested in. Stay safe!
I completely agree with the article’s emphasis on cryptocurrency security! Ensuring your digital assets are protected is crucial in today’s environment. Using secure wallets and maintaining strong passwords should be a priority for every investor. It’s all about being proactive to keep our investments safe from potential threats.
I completely agree that protecting your cryptocurrency is crucial. With the ever-evolving landscape of digital assets, ensuring we use secure wallets and strong passwords can really make a difference. It’s not just about the blockchain’s security; we have to be proactive as investors. The stakes are too high to take any chances!
I completely agree with the emphasis on security measures for cryptocurrency! It’s alarming how easily hackers can exploit vulnerabilities if we don’t take precautions. Using strong passwords and secure wallets is a must. My friends always underestimate the importance of these basics, but I’ve seen too many people lose their investments due to negligence. We need to prioritize our digital safety just like we do in the real world!
What additional security measures do you recommend for someone just starting with cryptocurrency?
Hi SarahTechie92! For beginners, I highly recommend enabling two-factor authentication (2FA) for your accounts. It adds an extra layer of security beyond just a password. Also, consider using a hardware wallet for storing your crypto, as it keeps your assets offline and secure from online threats. Staying informed about security practices is key to protecting your investments!
I completely agree with the article! Protecting your cryptocurrency is crucial, especially with how hackers are becoming more sophisticated. Using a secure digital wallet should be a no-brainer for anyone investing in crypto. I also think we need to spread awareness about using strong, unique passwords—it’s a simple yet effective way to add an extra layer of security.
What additional security measures do you recommend for someone new to cryptocurrency investment?
Hi Jessica_CryptoGuard! For beginners, I recommend enabling two-factor authentication on your accounts and considering hardware wallets for storing larger amounts of cryptocurrency. It’s also wise to stay updated on the latest security practices, as the landscape is constantly evolving.
Great article on cryptocurrency security! What specific features should I look for in a secure digital wallet?
What are some recommended practices for creating strong and unique passwords for my cryptocurrency accounts?
I completely agree with the article’s emphasis on cryptocurrency security. It’s essential to take proactive steps to protect our digital assets. A secure digital wallet and strong passwords are a must! With so much at stake, we can’t afford to be careless about our investments. Let’s stay safe out there!
I completely agree with the importance of securing your cryptocurrency. With how quickly things are evolving in the digital space, safeguarding our assets should be our top priority. Implementing strong passwords and using secure wallets are essential practices we all need to adopt. It’s better to be safe than sorry in this ever-changing landscape!